The dark web exists as a persistent, shadowy corner of our digital lives. It’s a topic of immense curiosity, particularly for those interested in cybersecurity and hacking. While often sensationalized, it is a very real place where a grim and sophisticated economy thrives. One of the most active markets within this economy is the trade of stolen data—the personal and corporate information harvested from data breaches around the globe.
But how does it actually work? How does a cybercriminal go from a data breach to a sold database? This isn’t a “how-to” guide. Engaging in these activities is illegal and harmful. Instead, this is a legal and educational explanation of the process, designed to shed light on the mechanics of this underground economy. By understanding the workflow, we can better appreciate the threats and learn how to protect ourselves from becoming another entry in a stolen database.
This article will walk you through the entire lifecycle of a data transaction on the dark web, from the breach itself to the final sale, all from a safe and legal perspective based on publicly available information and the methods used by cybersecurity researchers to monitor these threats.
Disclaimer: This article is for educational purposes only. Accessing the dark web is not in itself illegal, but using it to purchase or sell stolen data or engage in any other illicit activity is a serious crime with severe consequences. This information is intended to educate and raise awareness, not to instruct.
The Ecosystem: More Than Just a Marketplace
Before diving into the workflow, it’s crucial to understand that the dark web is not one giant “bad guy store.” It’s a complex ecosystem of different platforms, each serving a specific purpose. Transactions involving leaked databases typically span several of these areas.
- Hacking Forums & Communities: These are the social hubs. Before a sale even happens, this is where hackers might boast about a recent breach, seek partners, or sell the “access” that would allow another criminal to exfiltrate the data themselves.
- Leak Sites: Often run by ransomware gangs, these are non-commercial sites. Their purpose is to publish the names of their victims and threaten to leak their data if a ransom is not paid. Sometimes, if the ransom isn’t met, small samples or the entire database will be dumped here for free to damage the victim’s reputation and prove the gang’s credibility.
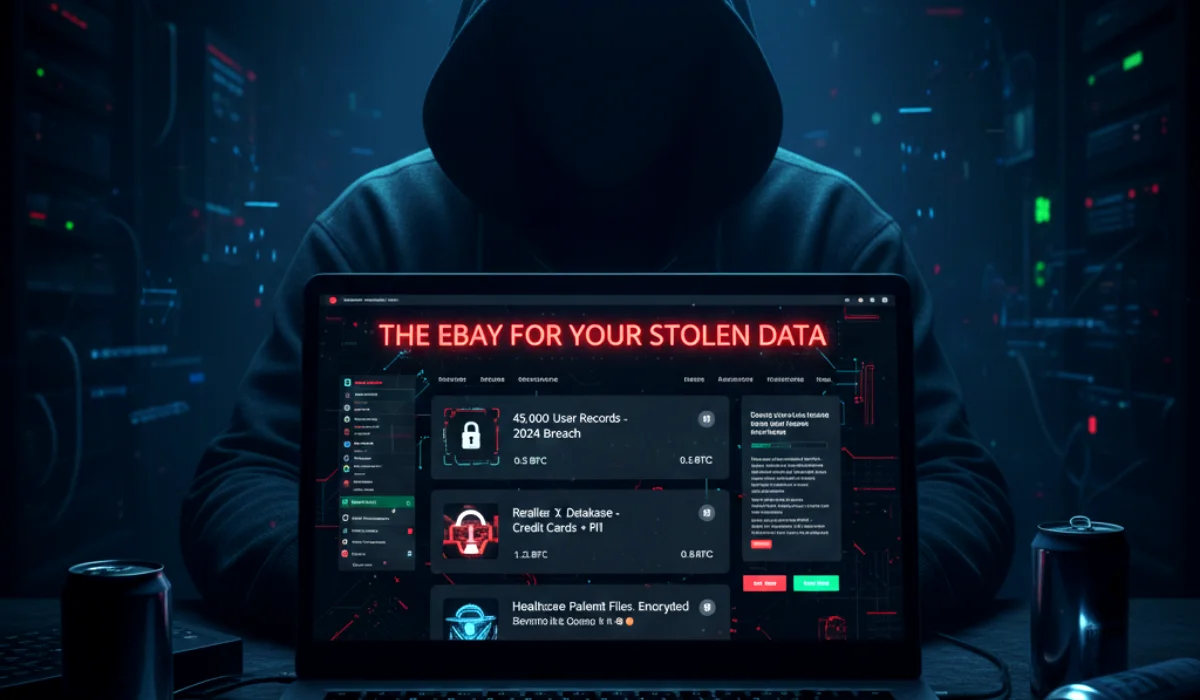
- Marketplaces: These are the e-commerce platforms of the dark web. They look and feel surprisingly like legitimate sites like eBay or Amazon, complete with vendor profiles, user ratings, escrow services, and customer support. This is where a database that has been stolen is most often listed for sale.
- Encrypted Chat Channels (e.g., Telegram): Much of the initial negotiation, “customer service,” and planning happens in private, encrypted channels. These offer a more direct line of communication between sellers and serious buyers.
The Complete Workflow: From Breach to Bitcoin
The process of a database making its way from a secure server to a hacker’s hard drive follows a grimly predictable path. Here is the step-by-step process, explained from an observational, cybersecurity perspective.
Step 1: The Breach and Exfiltration
It all starts with a vulnerability. A cybercriminal gang exploits a weakness in a company’s security system—this could be anything from an unpatched server to a successful phishing attack on an employee. Once they have a foothold, their primary goal is “data exfiltration”—the act of secretly copying and removing the data from the company’s network.
This is a delicate process. They must move massive amounts of data without tripping any automated security alerts. Once the data is successfully copied, it is stored on the attacker’s secure servers, ready for the next stage.
Step 2: The “Marketing” and Listing
A stolen database is worthless if no one knows it’s for sale. The seller must now advertise their product.
- Creating a Listing: The seller will create a new listing on a reputable dark web marketplace (names like “RussianMarket” or “BidenCash” have been prominent). This listing will read like a product description, containing key details to entice buyers:
- Source: The name of the breached company (e.g., “Major Retailer X”).
- Freshness: The date of the breach (e.g., “Fresh 2025 Breach”). Newer data is far more valuable.
- Size: The number of records (e.g., “45,000 User Records”).
- Content: What the data includes (e.g., “Includes Email, Password (Hashed), Full Name, Address, Payment Info”).
- Price: The asking price, almost always in a cryptocurrency like Bitcoin or Monero for anonymity. Prices can range from a few hundred dollars to tens of thousands, depending on the quality and richness of the data.
- Providing Proof: No one trusts anyone on the dark web. To prove the data is legitimate, the seller will often provide a small, redacted sample of the data for free. They might also share a screenshot of the database structure or a few rows of non-sensitive information.
Step 3: The Negotiation and Purchase
A potential buyer who sees the listing will not just click “buy.” They will typically engage with the seller first, often moving to an encrypted chat platform.
- Vetting: The buyer will ask questions to verify the data’s authenticity. The seller will, in turn, vet the buyer to ensure they aren’t a security researcher or law enforcement.
- Negotiation: The price is often negotiable. A bulk buyer or a “repeat customer” might get a discount.
- The Escrow System: This is the most critical part of the transaction. To prevent scams (which are rampant), reputable marketplaces use a multi-signature escrow system. The buyer sends the cryptocurrency not to the seller, but to a secure digital wallet controlled by the marketplace. The funds are only released to the seller after the buyer confirms they have received the data and that it is as described. This system builds a fragile sense of trust and mimics the buyer protection of legitimate e-commerce.
Step 4: The Delivery
Once the payment is in escrow, the seller delivers the database. This is never done via email. The seller will upload the (often massive) database file to a secure, anonymous file-hosting service and send the encrypted download link and decryption key to the buyer.
After the buyer downloads the file and confirms its contents match the listing’s description, they will notify the marketplace. The marketplace then releases the funds from escrow to the seller’s wallet, and the transaction is complete. The marketplace takes a small percentage (typically 1-5%) as their commission.
Step 5: The Aftermath – What the Buyer Does Next
The buyer doesn’t purchase a database to let it sit. The data is a raw material for a wide range of cybercrimes:
- Phishing & Social Engineering: The names and emails are used to launch highly targeted phishing campaigns.
- Credential Stuffing: The username/password pairs are used in automated attacks to try and break into other accounts across the web (banking, social media, etc.), preying on the fact that people reuse passwords.
- Identity Theft & Financial Fraud: With names, addresses, and other personal details, criminals can open lines of credit, file fraudulent tax returns, or commit other forms of identity theft.
- Resale: Sometimes, the buyer is a wholesaler who will break the large database into smaller, more specific chunks and resell them on other marketplaces for a profit.
The Risks and Consequences: Why This Is a Losing Game
While the process described above may sound organized, it is fraught with peril for everyone involved, and the ultimate victims are the individuals whose data was stolen.
- For the Buyer: There is a very high risk of being scammed. Many listings are fake, and even with escrow, a seller can deliver a file full of garbage data. Furthermore, law enforcement agencies are actively monitoring these marketplaces. Making a purchase leaves a digital trail that can lead to arrest and prosecution.
- For the Seller: While they may make a profit, they place themselves at the top of law enforcement’s target list. The takedowns of major marketplaces like “Silk Road” and “AlphaBay” prove that anonymity is not guaranteed.
- For the Victim: The consequences are devastating and long-lasting. Victims of data breaches face years of battling identity theft, financial fraud, and the psychological stress of having their private information exposed. The loss of trust in the breached company is immense, and in cases involving medical or biometric data, the damage can be irreparable.
Conclusion: Knowledge as a Defense
Understanding the cold, methodical process of how our data is bartered and sold on the dark web is not about learning to be a hacker. It’s about learning how the enemy operates. We see that stolen data is not just “lost”; it is packaged, marketed, and sold in a sophisticated underground economy.
This knowledge demystifies the dark web, stripping it of its sensationalism and revealing it for what it is: a criminal enterprise with real-world consequences. By understanding the value that criminals place on our data, we are better equipped to protect it. It reinforces the critical importance of strong, unique passwords, two-factor authentication, and holding companies accountable for the security of the information we entrust to them. The best way to devalue a stolen database is to make the data within it useless, and that defense starts with us.
Frequently Asked Questions (FAQs)
1. Is it illegal to browse the dark web?
No. Simply using the Tor browser to access the dark web is not illegal in most countries. However, engaging in or attempting to engage in any illegal activity is a crime.
2. How do cybersecurity companies monitor the dark web?
They use a combination of automated crawlers that scan marketplaces for keywords (like a company’s name) and human intelligence analysts who safely and anonymously navigate these forums to gather information on emerging threats.
3. What is the most commonly sold type of data?
Access credentials (usernames and passwords) are the most common and versatile type of data sold, as they are the key to unlocking other, more valuable information.
4. How much is my personal data worth?
Individually, not much. A single credit card number might sell for a few dollars. The real value comes from large, aggregated databases that can be used for wide-scale attacks.
5. What is an “escrow” service on the dark web?
It’s a system where a trusted third party (the marketplace administrator) holds the buyer’s payment until the seller has delivered the goods as promised. This is designed to prevent scams.
6. What cryptocurrencies are most commonly used?
Bitcoin is the most well-known, but privacy-focused coins like Monero are increasingly preferred because they make transactions much harder to trace.
7. Can law enforcement track transactions on the dark web?
Yes. While it is difficult, law enforcement agencies have developed sophisticated techniques to de-anonymize users and trace cryptocurrency transactions, leading to numerous arrests.
8. What is a “ransomware leak site”?
It’s a website used by ransomware gangs to publicly name their victims and leak their stolen data if the ransom demand is not paid. This is a “double extortion” tactic.
9. What is the difference between the “dark web,” “deep web,” and “surface web”?
The “surface web” is the public internet indexed by search engines. The “deep web” is anything not indexed (like your private email inbox or a corporate intranet). The “dark web” is a small, specific part of the deep web that requires special software like Tor to access and is designed for anonymity.
10. How do sellers build a “reputation” on these marketplaces?
Just like on eBay, they have public profiles with ratings and reviews from past buyers. A seller with a long history of positive reviews is seen as more trustworthy.
11. What is a “fullz”?
This is dark web slang for a “full package” of an individual’s identity information, typically including their name, address, Social Security number, date of birth, and sometimes bank account numbers.
12. Why do hackers sell data instead of using it themselves?
Different cybercriminals specialize in different areas. A hacker who is skilled at breaching networks may not be skilled at financial fraud. Selling the data is a way to quickly and easily monetize their illegal access.
13. What should I do if I suspect my data is on the dark web?
Immediately change the passwords for your important accounts (email, banking), enable two-factor authentication on all services that offer it, and consider using a credit monitoring service to watch for signs of identity theft.
14. What is “pogo-sticking” in the context of dark web monitoring?
This is a term used to describe the actions of security researchers or law enforcement who quickly “hop” between different dark web sites to gather intelligence without engaging in any transactions.
15. Is it possible to get scammed as a buyer on the dark web?
Yes, it is extremely common. Many listings are from scammers trying to take advantage of other criminals. There is no honor among thieves.
16. What is the single biggest misconception about the dark web?
That it is a magical, untraceable place. It is simply a network that provides a higher degree of anonymity, but skilled investigators can and do unmask users.
17. What is “double extortion”?
It’s a ransomware tactic where attackers not only encrypt the victim’s files but also steal a copy of the data and threaten to leak it publicly if the ransom isn’t paid.
18. Why don’t companies just pay the ransom?
Paying the ransom does not guarantee the data will be returned or deleted, it funds criminal enterprises, and it marks the company as a willing payer, making them a target for future attacks.
19. How can I protect myself from being part of a data breach?
Use strong, unique passwords for every website, enable two-factor authentication, be wary of phishing emails, and limit the amount of personal information you share with online services.
20. Is discussing this topic legally risky?
No. Discussing and educating others about the mechanics of dark web activities from a public interest and security awareness perspective is a legitimate and important part of cybersecurity journalism and research.