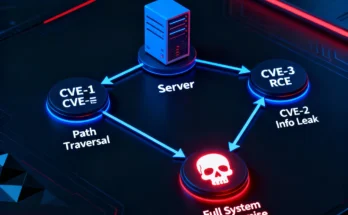
Web Server Hacking 2025: Automated Vulnerability Chain Exploitation from Reconnaissance to Shell
Web servers remain the internet’s frontline, processing billions of requests daily and holding the keys to our most sensitive data. As such, they are the …
Web Server Hacking 2025: Automated Vulnerability Chain Exploitation from Reconnaissance to Shell Read More