By a Cloud Security Architect specializing in AI/ML Infrastructure Security
TECHNICAL GUIDE – November 1, 2025
As enterprises race to deploy generative AI, they are confronting a critical, and often overlooked, question: “How do we secure the AI itself?” When our team deployed our first large language model-based chatbot into a production environment, I realized our traditional security frameworks for networks and applications were completely inadequate for this new paradigm. We had no visibility into the AI’s “inventory,” no specific controls for its unique vulnerabilities, and no playbook for responding to an AI-specific attack. This is the exact security gap that Google Cloud AI Protection is designed to fill.
Announced in April 2025 and continually enhanced since, Google Cloud AI Protection is not just another security tool; it’s a comprehensive framework designed to discover, secure, and manage the unique threats facing enterprise AI systems. As organizations make AI mission-critical, defending against threats like data poisoning, adversarial attacks, and AI model theft is no longer optional—it is a fundamental requirement for survival. This guide will provide a technical deep dive into what Google Cloud AI Protection is, the threats it mitigates, and how to implement it to secure your AI investments.cloud.google+1
The Modern AI Threat Landscape: Beyond Traditional Cybersecurity
Securing AI is not the same as securing a traditional web server. The attack vectors are more subtle and potentially far more devastating.
- Data Poisoning: This is one of the most insidious threats. Attackers inject carefully crafted malicious data into your training datasets. This “poisons” the model at its core, causing it to learn incorrect patterns. A medical imaging AI trained on poisoned data could learn to misdiagnose cancer, or a financial fraud model could learn to ignore a specific type of fraudulent transaction.
- Adversarial Attacks: These attacks exploit the “blind spots” in a machine learning model. By making subtle, often imperceptible, perturbations to an input, an attacker can cause the model to make a wildly incorrect classification. A classic example is a self-driving car’s AI misinterpreting a stop sign that has been modified with a few small stickers.
- Model Extraction (Model Theft): Proprietary AI models are incredibly valuable intellectual property. Attackers can use a “model stealing” attack, making thousands of carefully structured API calls to your AI application to reverse-engineer and steal the underlying model’s architecture and weights.
- Model Inversion: An attacker can analyze a model’s outputs to infer sensitive information from its training data. For example, by probing a fraud detection model, an attacker could potentially reconstruct credit card numbers or personal identifiable information (PII) that were used during training.
- Prompt Injection: This is a direct attack on large language models (LLMs). Attackers craft malicious prompts designed to bypass the model’s safety guardrails, tricking it into revealing sensitive information, generating harmful content, or executing unintended commands. Our guide on Prompt Injection Defense explores this in detail.
Google Cloud’s Cybersecurity Forecast report identified the attacker’s use of AI as a top threat, making defensive AI capabilities essential.infoq
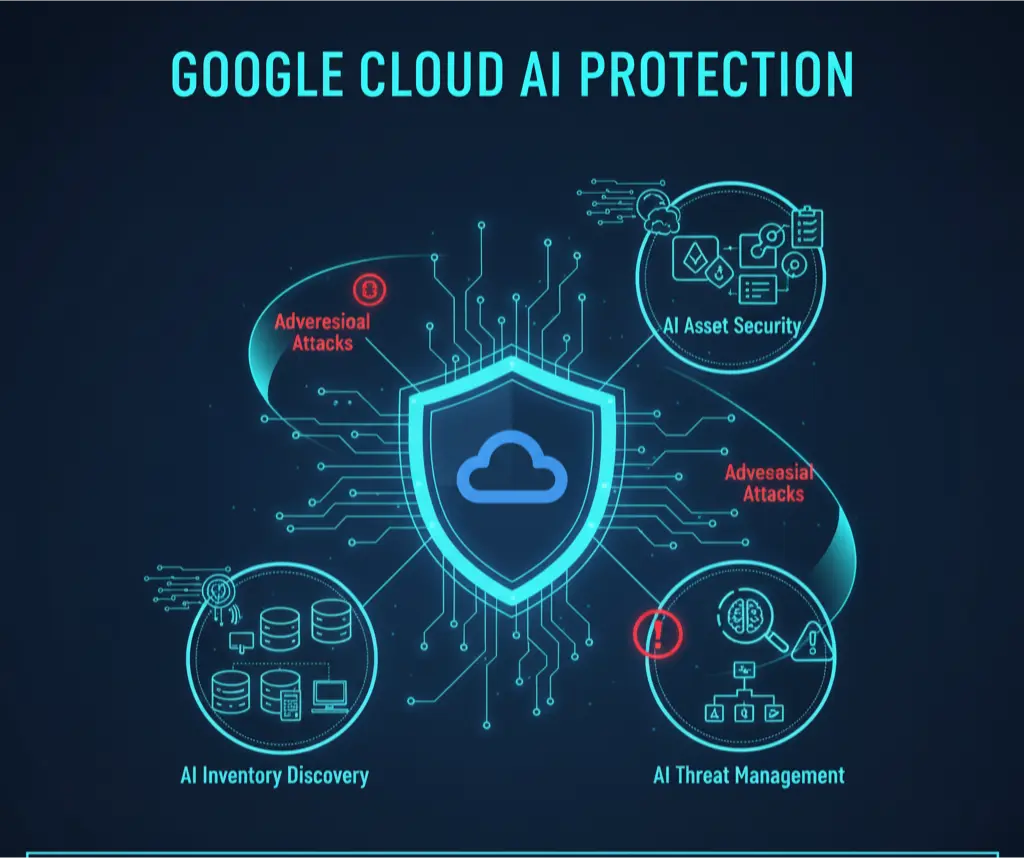
What is Google Cloud AI Protection? The Three Pillars of AI Security
Google Cloud AI Protection is a suite of services, deeply integrated into the Google Cloud ecosystem, built on three core capabilities designed to address the entire AI lifecycle.discuss.techlore+1
| Core Capability | Function | Why It Matters |
|---|---|---|
| 1. Discover AI Inventory | Automatically discovers and catalogs all AI assets: models, applications, and datasets across your Google Cloud environment, mapping their relationships. | You cannot secure what you cannot see. This provides a complete inventory of your AI “attack surface.” |
| 2. Secure AI Assets | Applies security classifications, access controls, and data protection policies to models and datasets. Integrates with Sensitive Data Protection for PII detection. | Prevents unauthorized access to unencrypted models or sensitive training data, stopping AI model theft at the source. |
| 3. Manage Threats | Uses behavioral analytics to detect, investigate, and respond to AI-specific threats like unusual model access, data anomalies, or adversarial inputs. | Provides real-time threat detection for AI and enables automated remediation, crucial for AI-speed attacks. |
Let’s break down these pillars. Model Armor, a key component, provides real-time, in-line protection for prompts and responses, defending against prompt injection and data leakage as they happen. The Data Security Posture Management (DSPM) capabilities extend discovery and classification to AI training data, helping to prevent data poisoning before it starts.siliconangle+2
Integration with Security Command Center (SCC): A Unified View of Risk
Crucially, Google Cloud AI Protection is not a standalone product. It is deeply integrated into Google Cloud Security Command Center (SCC), Google’s centralized security and risk management platform. This integration is what makes it so powerful for enterprise security teams.siliconangle+1
- Unified Visibility: AI security risks are not viewed in a silo. They are presented alongside your other cloud security risks (like
cloud security misconfigurations), giving you a holistic view of your security posture. - Risk Contextualization: SCC contextualizes AI-specific threats. For example, it can identify a “toxic combination” of risks: a publicly exposed Vertex AI endpoint running a model trained on unvetted, sensitive data.
- Automated Red Teaming: The platform includes capabilities for virtual red teaming, simulating attacks like
data poisoningandadversarial attacksagainst your models in a sandboxed environment to identify vulnerabilities before they can be exploited. For more on this, see our Adversarial ML Playbook. - Prioritized Remediation: SCC doesn’t just find problems; it provides prioritized, actionable recommendations to fix them, integrating with ticketing systems and infrastructure-as-code pipelines.
Threat Scenarios & How Google Cloud AI Protection Responds
Let’s walk through how Google Cloud AI Protection mitigates real-world threats.
Scenario 1: Supply Chain Data Poisoning Defense
- Attack: An attacker compromises a third-party data vendor and injects thousands of subtly manipulated images into a dataset destined for training your medical imaging AI.
- Detection: As the dataset is ingested into Vertex AI, the DSPM component of AI Protection scans it. It detects statistical anomalies and a drift from the expected data distribution, flagging the dataset as potentially poisoned.
- Response: The system automatically quarantines the dataset, prevents it from being used for training, and raises a high-priority alert in SCC, detailing the nature of the detected anomaly.
Scenario 2: Model Extraction Security
- Attack: An attacker, posing as a regular user, begins making thousands of API calls to your new commercial LLM, carefully crafting queries to reverse-engineer the model’s weights.
- Detection: The threat management pillar of AI Protection uses behavioral analytics to detect an anomalous access pattern: an extremely high volume of queries from a new IP address, with query structures that match known
AI model thefttechniques. - Response: The system automatically rate-limits the attacker’s IP, triggers a requirement for step-up authentication (like solving a complex CAPTCHA), and alerts the SOC.
Scenario 3: Insider Threat – Model Theft
- Attack: A disgruntled data scientist with legitimate access to a proprietary trading algorithm model attempts to download the model files to a personal device before leaving the company.
- Detection: AI Protection logs all model access events. The unusual download of the entire model’s weights, outside of normal CI/CD processes, triggers a high-severity alert in SCC.
- Response: The alert triggers an automated response playbook: the user’s access is immediately revoked, and Data Loss Prevention (DLP) rules are enforced to block the exfiltration of the model files from the corporate network.
Implementation Roadmap: A Phased Approach
Deploying Google Cloud AI Protection should be a structured process.
Phase 1: Inventory & Discovery (Weeks 1-2)
- Enable AI Protection in SCC to run a full discovery scan of your Google Cloud organization.
- Catalog all existing AI assets: Vertex AI models, BigQuery datasets, AI Platform applications.
- Classify these assets by risk level (e.g., a customer-facing chatbot is “Critical,” an internal research model is “High”).
Phase 2: Secure & Harden (Weeks 3-4)
- Use the DSPM capabilities to scan all training datasets and apply sensitivity labels. Enable automatic PII redaction.
- Configure IAM policies to enforce the principle of least privilege for
Vertex AI security. - Enable Model Armor for all production-facing AI applications to provide real-time
prompt injection defense.
Phase 3: Monitor & Detect (Weeks 5-8)
- Enable all AI-specific threat detection modules within SCC.
- Configure alerting rules to notify your SOC of high-severity events like suspected
data poisoningormodel extractionattempts. - Build dashboards for ongoing visibility into your AI security posture.
Phase 4: Respond & Govern (Ongoing)
- Develop and test AI-specific
incident responseplaybooks. - Train your security team on how to investigate AI security alerts.
- Incorporate AI security into your overall
AI governanceframework, defining policies for acceptable use and security baselines.
Conclusion: The New Baseline for Enterprise AI
The proliferation of generative AI has created a new and dangerous attack surface that traditional security tools were not built to handle. Google Cloud AI Protection provides the industry’s most comprehensive, cloud-native solution for securing the entire AI lifecycle. In an era where AI models are making mission-critical business decisions, their security is synonymous with business continuity. Organizations that proactively implement a robust AI security framework like this will build trust, mitigate risk, and gain a significant competitive advantage. Those that don’t are not just risking a data breach; they are risking the integrity of their entire AI-driven future. The time to act is now.
SOURCES
- https://euro-security.de/en/google-cloud-security-summit-2025-new-security-features-for-defenders-and-secure-ai-innovations/
- https://docs.cloud.google.com/release-notes
- https://cloud.google.com/blog/products/identity-security/driving-secure-innovation-with-ai-google-unified-security-next25
- https://techwireasia.com/2025/08/google-cloud-expands-ai-security-tools-at-2025-summit/
- https://siliconangle.com/2025/08/19/google-cloud-adds-new-protections-ai-agents-cloud-workloads-security-summit-2025/
- https://discuss.techlore.tech/t/new-al-protection-from-google-cloud-tackles-al-risks-threats-and-compliance/12812
- https://www.itsecuritydemand.com/news/security-news/google-unveils-new-ai-security-capabilities-at-cloud-security-summit-2025/
- https://www.infoq.com/news/2025/03/gcp-ai-protection-security/
- https://nexttechtoday.com/news/google-cloud-unveils-ai-driven-security-tools/
- https://ai.google/static/documents/ai-responsibility-update-published-february-2025.pdf


