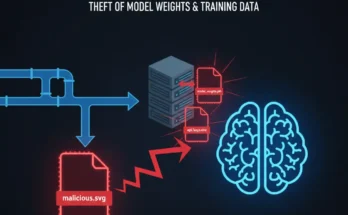
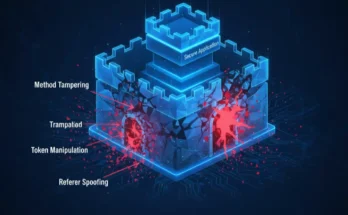
Session Hijacking 2025: The Complete Guide to AI Attacks & Defense
Session hijacking, a foundational topic in ethical hacking and a core component of CEH Module 11, was supposed to be a “solved” problem. The widespread …
Session Hijacking 2025: The Complete Guide to AI Attacks & Defense Read More