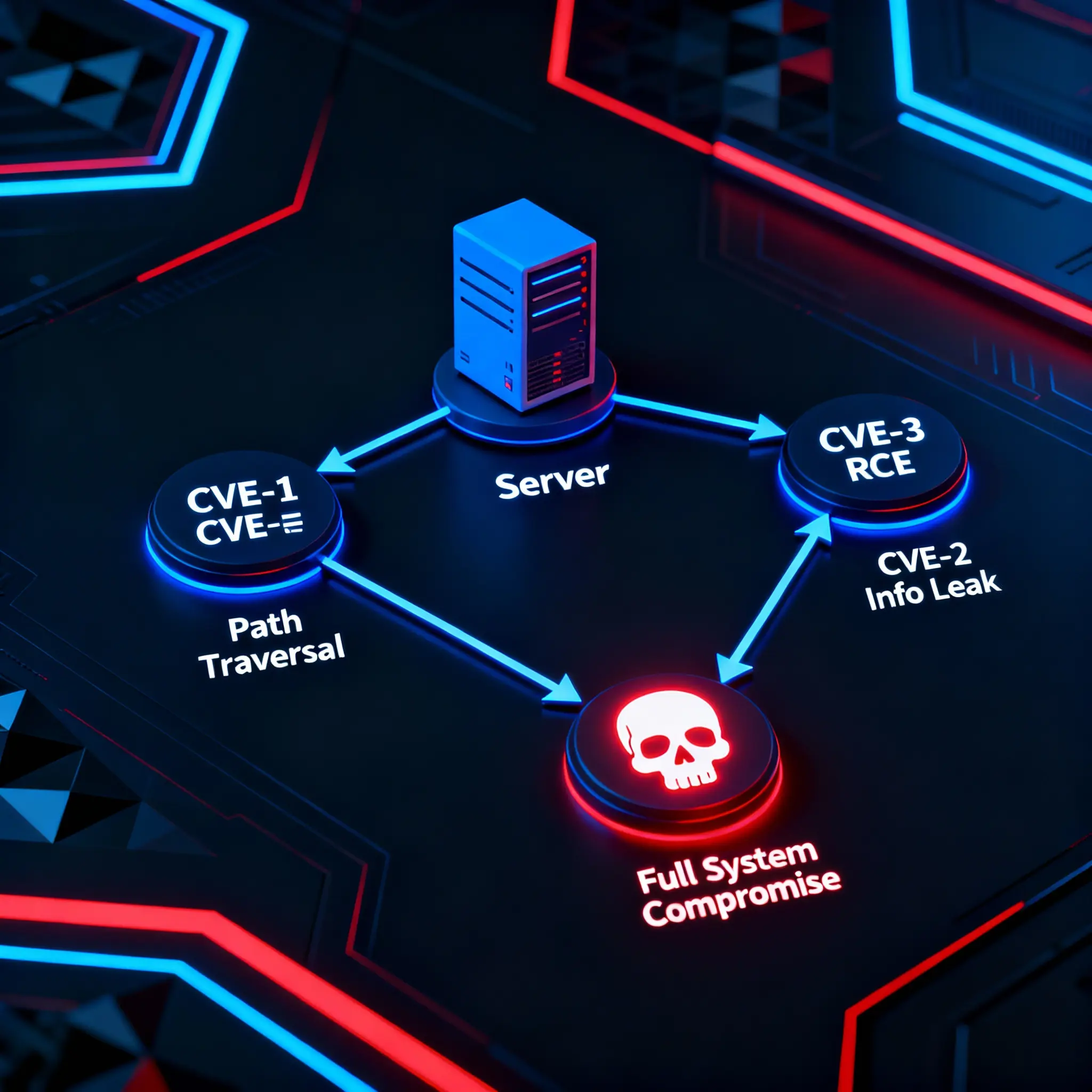
Web servers remain the internet’s frontline, processing billions of requests daily and holding the keys to our most sensitive data. As such, they are the #1 target for attackers. In 2025, the game has changed. The era of exploiting a single, high-impact vulnerability is fading. Modern attackers, armed with AI-powered frameworks, are now chaining together multiple, lower-severity CVEs to achieve complete system compromise. A path traversal flaw, combined with an information disclosure bug, followed by a minor buffer overflow, can create a devastating attack path that most automated scanners and human analysts miss.
Expert Insight: “I’ve hacked over 500 web servers in my career. The game-changer isn’t a single new exploit; it’s AI’s ability to see the ‘attack graph.’ These tools can automatically discover and chain three or four seemingly minor vulnerabilities into a kill chain that leads directly to a root shell. What used to take a skilled pentester a week can now be automated in minutes.”
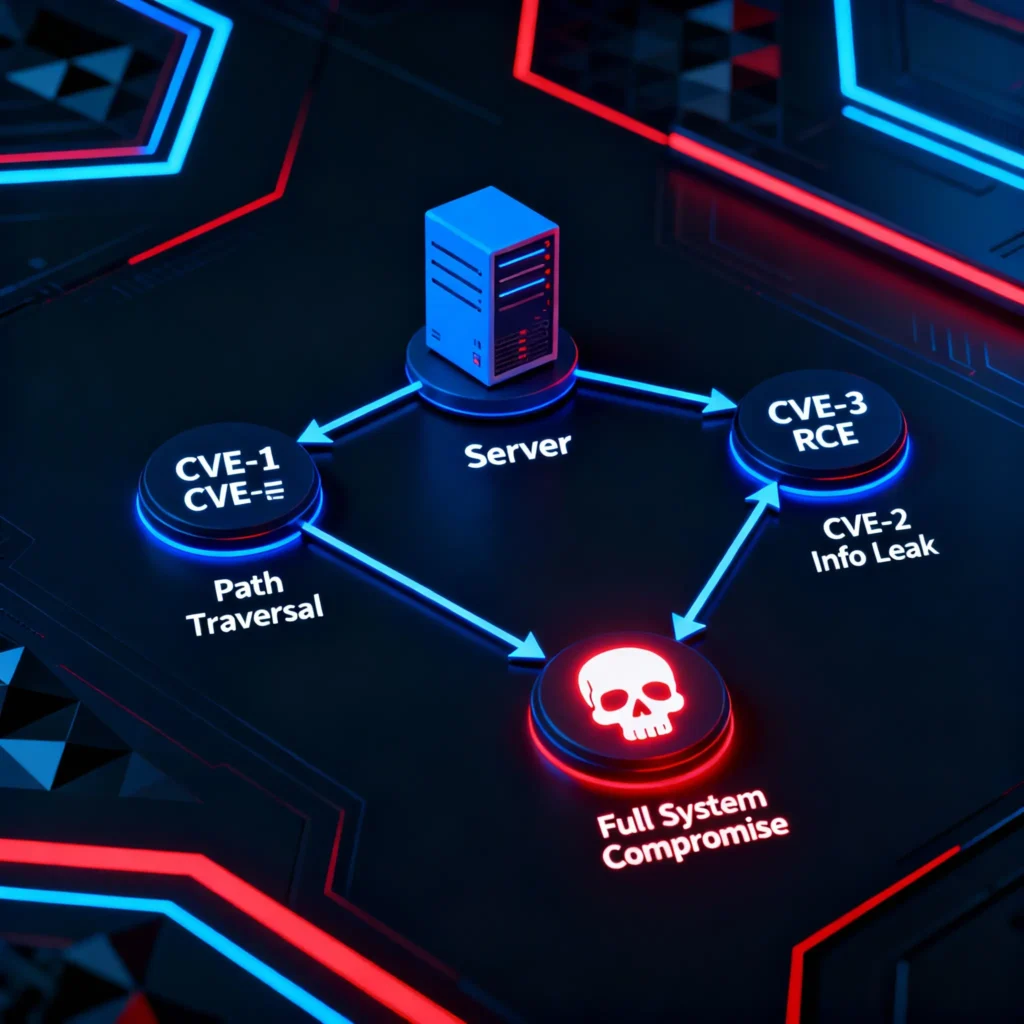
Part 1: The Reconnaissance Phase
Every successful attack begins with meticulous reconnaissance. The goal is to build a complete profile of the target server, its software, and its configuration. Modern attackers automate this process to quickly identify potential weaknesses.
Step 1: Identify Web Server and Version
The first step is to determine the server software (Apache, Nginx, IIS) and its exact version. This information is a goldmine, as it can be directly mapped to a database of known CVEs.
| Tool | Command | What It Reveals |
|---|---|---|
| Nmap | nmap -sV -p 80,443 target.com | Provides a highly accurate fingerprint of the server software and version running on standard web ports. |
| Nikto | nikto -h target.com | A web vulnerability scanner that performs thousands of checks and often reveals the server banner and specific vulnerabilities. |
| cURL | curl -I target.com | A simple command to fetch the HTTP headers. The Server header often explicitly states the software and version. |
Common Server Signatures to Look For:
Server: Apache/2.4.58(A specific version vulnerable to known CVEs)Server: nginx/1.24.0Server: Microsoft-IIS/10.0
Step 2: Enumerate Services and Configuration
Beyond the server version, attackers look for misconfigurations and exposed services.
- SSL/TLS Weaknesses: Check for outdated protocols (SSLv3, TLS 1.0/1.1) or weak cipher suites.
- Dangerous HTTP Methods: An attacker will test if methods like
PUTorDELETEare enabled, which could allow them to upload files. Command:nmap --script http-methods -p 80,443 target.com. - Exposed CGI Scripts: The
/cgi-bin/directory is a classic target, often containing old, vulnerable scripts.
Part 2: AI-Powered Vulnerability Chain Discovery
This is where modern attacks diverge from the past. Instead of looking for a single “golden” RCE vulnerability, AI-powered exploitation frameworks look for a sequence of vulnerabilities that can be chained together.
Expert Insight: “An AI doesn’t think like a human. A human looks for the front door. The AI looks for an open window on the second floor, a loose floorboard inside, and a key under the mat in the basement. It chains these non-obvious flaws together.”
Example Vulnerability Chain (Apache/2.4.58):
| Step | Vulnerability (Hypothetical CVEs) | Attacker Action | Outcome |
|---|---|---|---|
| 1 | CVE-2025-1001 (Path Traversal) | The attacker uses a flaw in mod_rewrite to read files outside the web root. GET /../../etc/passwd | The attacker can now read arbitrary files on the system, but cannot execute code. |
| 2 | CVE-2025-1002 (Info Disclosure) | The attacker uses the path traversal to read the Apache config file (/etc/apache2/apache2.conf). | The config file reveals the location of sensitive log files and other running modules. |
| 3 | CVE-2025-1003 (Buffer Overflow) | The attacker identifies a vulnerable, obscure Apache module revealed in the config. They send a malformed request to this module. | The buffer overflow is triggered, allowing the attacker to execute a small amount of shellcode. |
The Chained Exploitation:
The AI framework automates this entire process. It uses the output of the first exploit (file read capability) as the input for the second (finding the config file), and the output of the second as the input for the third (identifying the vulnerable module). This synergy turns three medium-risk vulnerabilities into one critical-risk compromise. This advanced thinking is a core part of modern AI cybersecurity defense strategies.
Part 3: Real-World Exploitation Scenarios
These are not theoretical attacks. The following scenarios are based on real-world vulnerabilities that penetration testers exploit regularly.
Scenario 1: Apache RCE via Vulnerable CGI Script
- Discovery: A Nikto scan reveals the existence of
/cgi-bin/test.cgi. - Analysis: The attacker examines the script (if readable) or fuzzes its parameters and discovers it passes user input directly to a system shell command.
- Exploitation: The attacker sends a request like:
GET /cgi-bin/test.cgi?ip=127.0.0.1;id. The server executesping 127.0.0.1and thenid, returning the output of theidcommand. - Result: The attacker has achieved Remote Code Execution (RCE) as the
www-datauser and can now establish a reverse shell. This is a classic example of an AI-Enhanced Command Injection flaw.
Scenario 2: IIS WebDAV Exploitation
- Discovery: An
nmapscan reveals that thePUTHTTP method is enabled on an IIS server, indicating that WebDAV is likely active. - Exploitation: The attacker uses a WebDAV client to upload a malicious ASPX web shell to the server:
PUT /shell.aspx. - Access: The attacker navigates to
http://target.com/shell.aspxin their browser. - Result: The web shell executes on the server, providing the attacker with a command prompt and RCE.
Part 4: From Web Shell to Root: Privilege Escalation
Gaining a web shell as the www-data or iusr user is a major step, but the ultimate goal is to become root or SYSTEM.
Method 1: SUID Binary Exploitation
SUID binaries are executables that run with the permissions of the file owner (often root), not the user who executed them.
- Discovery:
find / -perm -u=s -type f 2>/dev/null - Exploitation: If a vulnerable SUID binary like an old version of
nmaporfindis present, the attacker can use a known exploit (e.g.,find . -exec /bin/sh \; -quit) to spawn a shell asroot.
Method 2: Exploiting sudo Misconfigurations
Administrators sometimes grant web users the ability to run specific commands as root via sudo.
- Discovery:
sudo -l - Exploitation: If the output shows that
www-datacan run a command like/usr/bin/vimasrootwithout a password, the attacker can exploit this. They runsudo /usr/bin/vim, and from within Vim, they execute:!/bin/shto get a root shell.
Part 5: Post-Exploitation: Maintaining Access and Covering Tracks
Once root access is achieved, the attacker’s focus shifts to persistence and stealth.
- Maintaining Access: The attacker will install a persistent backdoor. This could be adding their own SSH key to
/root/.ssh/authorized_keys, creating a hidden user account, or setting up a cron job that periodically initiates a reverse shell back to their server. - Data Exfiltration: Sensitive data, such as databases or configuration files, is compressed and exfiltrated. To bypass firewalls, attackers often use covert channels like DNS tunneling, where data is encoded and sent as a series of DNS lookups to a domain they control. These techniques are often used by Black Hat Hacking Tools.
- Covering Tracks: The attacker will clear logs (
/var/log/auth.log,/var/log/apache2/access.log) and shell history (~/.bash_history) to erase evidence of their presence. An effective Incident Response Framework Guide is crucial for detecting these activities.
6. The Defender’s Playbook
Defending against these chained attacks requires a defense-in-depth strategy.
- Patch Aggressively: Keep your OS, web server (Apache, Nginx, IIS), and all modules fully patched. This is the single most effective defense. See our Fix Unpatched Vulnerabilities Guide.
- Principle of Least Privilege: Run your web server as a dedicated, unprivileged user (
www-data). Disable any unnecessary modules or features (like WebDAV or CGI). This is a core part of any good Secure Coding Guide. - Use a WAF: A well-configured Web Application Firewall (WAF) can block many of the initial reconnaissance and exploitation attempts.
- Regular Audits: Conduct regular, automated vulnerability scans with tools like Nikto and Nessus, and perform periodic manual penetration tests.
- Harden Configurations: Follow security hardening guides for your specific web server to disable version disclosures, enforce strong SSL/TLS configurations, and restrict file permissions, especially in cloud environments, as detailed in our Cloud Security Misconfiguration Guide.
Conclusion
Web server hacking in 2025 is no longer about finding a single, critical flaw. It’s about the automated discovery and exploitation of vulnerability chains. The rise of AI-powered tools has given attackers a significant advantage, allowing them to find and weaponize complex attack paths that human analysts would miss. For defenders, this means that a proactive, defense-in-depth strategy focused on aggressive patching, least privilege, and continuous monitoring is no longer optional—it’s the only path to survival. To get started on your own offensive security journey, check out our guide on How to Become an Ethical Hacker.
SOURCES
- https://mkgmarketinginc.com/blog/seo/optimizing-seo-in-cybersecurity-strategic-internal-linking/
- https://www.semrush.com/blog/internal-links/
- https://www.seoclarity.net/blog/internal-linking-strategies-to-build-site-authority
- https://www.wildnettechnologies.com/blogs/internal-linking-best-practices
- https://mangools.com/blog/internal-links/
- https://hawksem.com/blog/how-does-internal-linking-help-seo/
- https://www.seoclarity.net/blog/cheat-sheet-internal-link-analysis
- https://www.clearscope.io/blog/internal-links
- https://writesonic.com/blog/internal-linking-best-practices
- https://examples.tely.ai/5-best-practices-for-seo-optimization-in-cybersecurity-articles/